Application/Network Security Assessment
Security testing in applications is the process of simulating a hacker-style attack on your app in order to detect and analyze security vulnerabilities that an attacker could exploit. As applications are critical to business success and an appealing target for cybercriminals. Application security testing is the proactive identification of vulnerabilities in applications, such as those that could result in the loss of sensitive user and financial information.
Network Security
Protecting your network from potential cyber threats effectively.


Application Security Assessment ( Web / Mobile / Desktop / Thick Client Based Application)
White Box Testing/Source Code Review/Static Application Security Testing
White box testing evaluates a software application's internal structure, code, and architecture to verify the input-output logic. This approach not only ensures functional accuracy but also enhances the application's design, security, and overall performance. In the context of web applications, this method is often called internal testing, clear box testing, open box testing, or glass box testing—terms that reflect the tester’s full visibility into the source code during the process


Application Security Assessment
( Web / Mobile / Desktop / Thick Client Based Application)
Gray Box Testing/Dynamic Application Security Testing (DAST)
Gray box testing is a hybrid software testing approach that blends elements of both black box and white box testing. It is commonly used in web application security testing, where the tester has partial knowledge of the application's internal code. This method helps uncover context-specific vulnerabilities and errors that may arise from flawed code structures or design inconsistencies.
Black Box Testing
Black Box, often referred to as behavioral testing or external testing, is a form of software testing technique wherein no prior knowledge of the internal code structure, implementation specifics, or internal routes of an application is necessary. It focuses on the application's input and output and is entirely dependent on the specifications and requirements for the software.


RED TEAMING SERVICES
Experience a real-world attack without any harmful results.
Get Secured against advanced cyber threats.
Get a full detailed report for your security strengths & weak points


CLOUD SECURITY SERVICES
Reconnaissance
Understand and identify gaps in infrastructure, architecture, data flow, policies, procedures etc
Analysis
Evaluation of controls, IAM, Infrastructure, security standards, data security, incident response & other related components to ensure security of cloud environment.
Recommendations
Suggestions and recommendations will be provided based on the gaps and risk identified during the assessment.
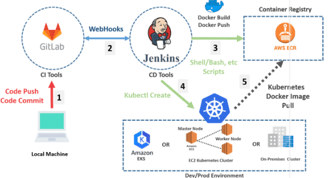
Container Security Services and Solutions
Containers are created out of layers of files. The container community often calls these files “container images.” The base image is the most important for security purposes because it is used as the starting point from which you create derivative images. Container security starts with finding trusted sources for base images. Even when using trusted images, though, adding applications and making configuration changes will introduce new variables. When bringing in external content to build your apps, you need to have proactive content management in mind.